By Maurizio di Paolo, technical writer based in Italy
The Internet of Things (IoT) has created a new ecosystem of connected electronic devices that communicate with each other to provide customised functionality in many fields, including medicine.
But as with other IoT devices, in medical ones the most significant challenges are in securing confidential information from unauthorised access. Hacker attacks are a serious threat, making an unsecure design a strong limitation for an IoT node or device. This requires a great deal of mathematics and microelectronic solutions, with cryptographic algorithms integrated into the systems.
Enormous Data Exchange
The amount of data IoT devices can generate is staggering. A US Federal Trade Commission report called “Internet of Things: Privacy & Security in a Connected World” found that just 10,000 families can generate terabytes of data, attracting hackers to all that sensitive information. When this is multiplied by millions of hyper-connected devices that use different technologies, the enormity of the challenge becomes very uncomfortable, indeed.
Performance and safety requirements vary widely from one application to another, and the success of smart homes, connected devices and cars, as well as industrial equipment, depends on the trust of users in robust and easy-to-use solutions with security features for absolute protection. The higher the volume of sensitive data transferred over the IoT and the IIoT, the higher the risk of data falsification, manipulation, theft and misuse.
This applies across all sectors, including medicine. The demand for improved, efficient health and medical services is worldwide, and technology takes centre stage. Wireless communication, micro- and nanoelectronics, battery power for devices, and more, are being harnessed to bring on earlier and more efficient treatment of patients, eventually shifting the way healthcare works, from diagnosis to prevention. But it is these same requirements, regulatory compliance and now security that also present challenges for developing and testing the newly-created, connected medical devices.
Security First
Many IoT devices use low-end microcontrollers (MCUs) with limited processing power and memory. Some devices have no user interface, and many are designed by OEMs with little or no Internet security. This leads to one of the most significant challenges to today’s IoT, enabling robust security for low-end devices.
Security features are primarily based on some core elements, including stable cryptographic cyphers, such as the Advanced Encryption Standard (AES), Secure Hash Algorithm (SHA), RSA (Rivest-Shamir-Adleman) and Elliptic-Curve Cryptography (ECC) public key.
SHA-1 is a hash algorithm, i.e. a one-way function, that is extremely difficult to invert. SHA-1 was designed by the US National Security Agency (NSA) and published by the National Institute of Standards and Technology (NIST) as a Federal Information Processing Standard (FIPS). It’s been widely used in applications for secure authentications, since it consists of a very complex set of functions that result in a unidirectional hash; see Figure 1.
Public-key cryptosystems verify the integrity and authenticity of the digital content (integrity refers to the digital content not changing since its creation, and authenticity indicates that an identified entity has released that content). These two fundamental characteristics are provided by the digital signature system to confirm that the digital content can be trusted.
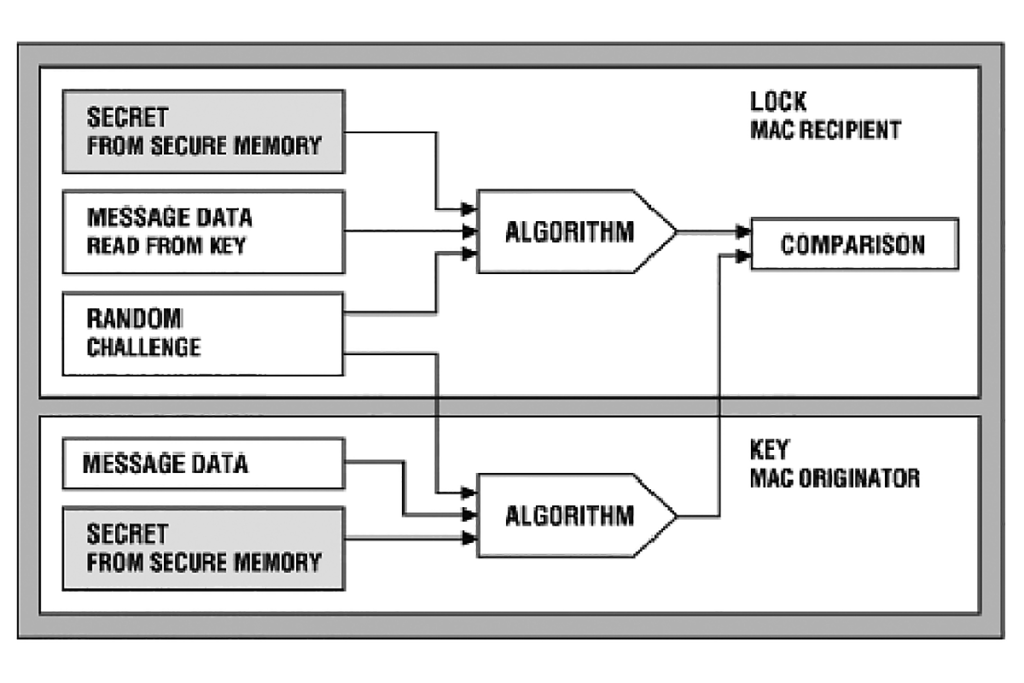
A decisive way to perform authentication in the digital world is the challenge-response method, which can be symmetric or asymmetric. Symmetric authentication is based on a shared secret, as shown in Figure 2.

The authentication based on asymmetric cryptography, instead, consists of two keys: private and public. The private key is known only by the device to be authenticated, whereas the public key can be revealed to any entity that wants to authenticate the device; see Figure 3.

Authentication ICs are configurable, fixed-functionality devices that provide a more efficient way of implementing challenge-response authentication, along with a compact set of cryptographic operations for active authentication. The SHA-256 safe authenticators use a 256-bit secret. The secure authenticator is a 1-wire slave with a unique 64-bit ROM ID that serves as a data element for authentication calculations.
Encryption MCUs
Microcontrollers support both symmetric and asymmetric encryption for digital signature and authentication, as well as cryptographic algorithms. They are equipped with hardware accelerators for SHA, RSA, ECDSA and AES, as well as with a complete encryption library that provides a turnkey API aligned to standards.
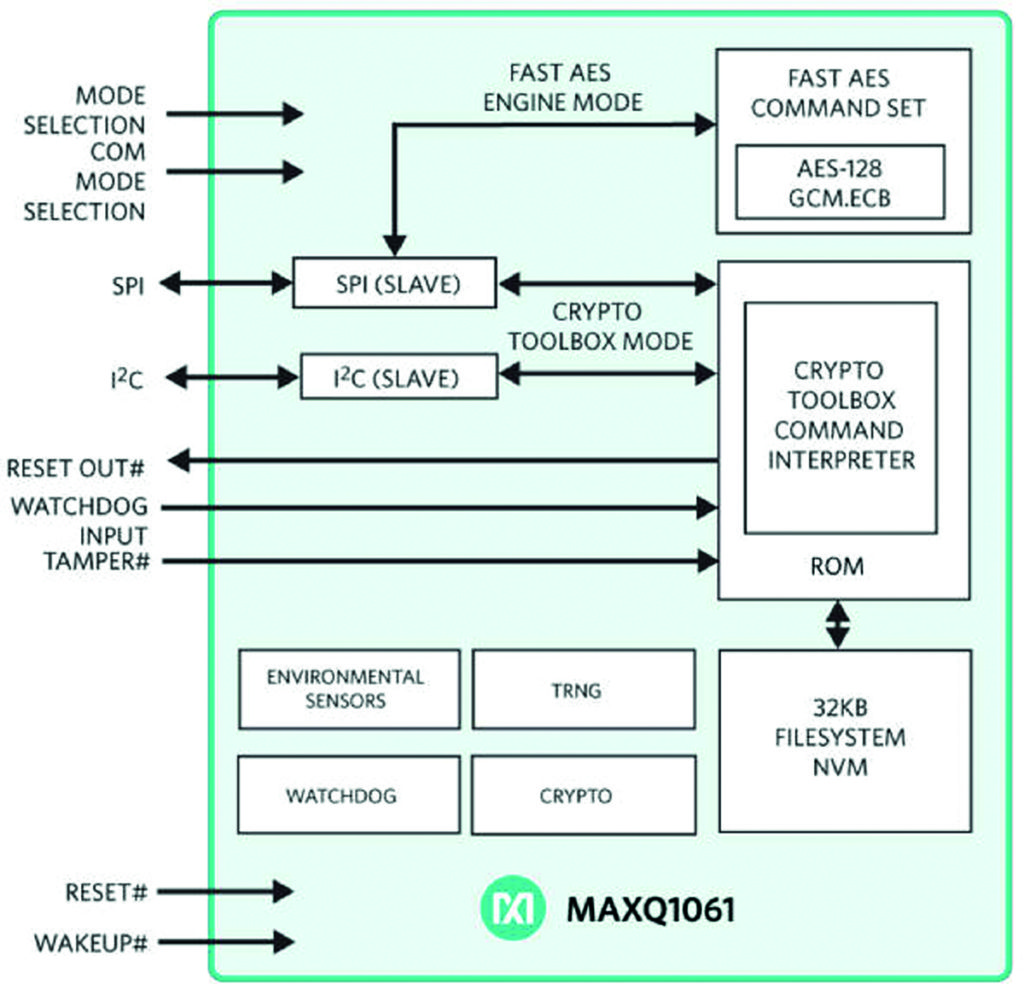
MAXQ1061 from Maxim Integrated (Figure 4) is a coprocessor that not only allows authentication but also manages the most critical steps of the TLS/SSL standard secure communication protocol over IP. Some solutions, such as MAX32626, have a hardware protection unit that supports AES authentication, and hardware for encryption, with integrated secure boot-up.
Modern MCUs have begun to include hardware accelerators, typically in the form of specialised peripherals, to simplify and speed up the processing, storage or transmission of sensitive data. For example, the Microchip PIC32MZ family (including PIC32MZ1024ECH100-I / PT) has a ‘crypto engine’ that accelerates common cryptographic functions.
Cryptographic processors are managed by a finite state machine using local storage of data packets. Atmel ATSHA204A-SSHDA-B, for example, provides secure authentication and validation for both host and client operations.
And CC3100 and CC3200 SimpleLink Wi-Fi devices from Texas Instruments offer an on-chip TLS stack with highly abstract and easy-to-use APIs, and integrated cryptographic hardware accelerators that quickly and efficiently perform complex computational tasks.
Some solutions implement a so-called “message digest that guarantees the integrity of the digital content”. This is a secure hash algorithm such as SHA-1, SHA-256 or SHA-3. A digest message is like a super-cyclic redundancy check (CRC), but it produces more outgoing bytes; for example, the SHA-256 algorithm produces a 32-byte output.
Maxim Integrated sells a series of devices that use a hardware implementation of SHA-256 to transfer data securely through a standard 1-wire interface. DS24L65 converts a standard I2C interface into a secure 1-wire that can then connect to a variety of 1-wire peripherals, such as the Maxim DS28EL22, with an on-chip SHA-256, 2kbit EEPROM and a unique 64-bit ID.
Equally, the Kinetis K6x NXP family of devices provides hardware acceleration for several standards, including AES and SHA. This coprocessor can run independent of the CPU and uses a memory interface mapped so commands and data can be stored in a cryptographic accelerator unit (CAU).
Elliptic-Curve Cryptography
In recent years, the ECC algorithm has widely spread across the security industry.
There are several types of this scheme:
- Elliptic curve digital algorithm (ECDSA): a digital signature algorithm primarily used to authenticate digital content and identify that content’s author.
- Elliptic curve integrated encryption scheme (ECIES): a hybrid encryption scheme that provides semantic security. System security is based on the Diffie-Hellman problem.
- Elliptical curve Diffie-Hellman (ECDH): allows two parts, each with public-private key pairs, to share a secret on an insecure channel.
The elliptical curve uses less computational resources than other versions, and has a reduced footprint. A secure application of RSA requires at least 2048 bits of security; RSA keys need 256 bytes. The equivalent ECC keys are only 224 bits long and the keys 28 bytes. There are two ECC from the Atmel CryptoAuthentication (Microchip) family of high-security hardware authentication devices: ATECC508A and ATECC108A. The ATECC508A is an ECDH encryption device for digital systems, specifically IoT nodes used in domotics (from the Latin word “domus” that means house, a combination of information technology, electronics and communications that makes a home “smart”), and medical, mobile and other applications; see Figure 5.

IC Security
Secure device authentication and enhanced encryption ensure the platforms are reliable. Maxim’s DeepCover safety ICs with ChipDNA technology provide adequate protection against invasive physical attacks. In addition to silicon, drivers and middleware, communication stacks and support are offered for rapid time-to-market development.
ChipDNA technology involves a physically unresolved (PUF) function that provides protection against invasive physical attacks, implementing advanced physical security to provide maximum low-cost IP protection, as well as clone prevention and device authentication.
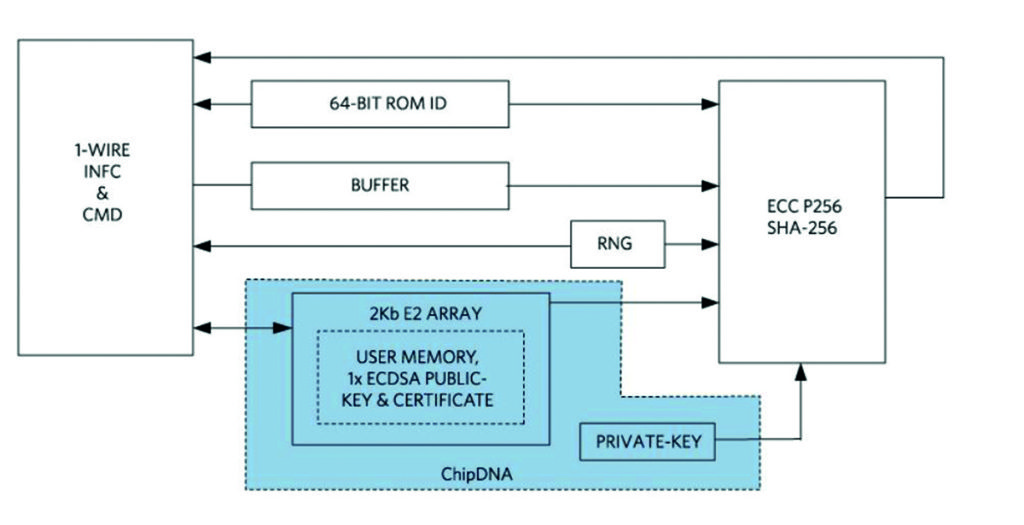
In the ChipDNA authenticators, the PUF circuit is based on random analogue characteristics of the device’s silicon to produce cryptographic keys, making it immune to all known invasive attack instruments and capabilities. In addition to security benefits, the ChipDNA simplifies or eliminates the need for secure IC key management; see Figure 6.
Attempts to probe or observe the ChipDNA modify the characteristics of the underlying circuit, preventing discovery of the unique value used by the chip’s cryptographic functions. Likewise, more exhaustive reverse-engineering attempts are thwarted because of the factory conditioning required to make the ChipDNA circuit operational.
The unique key is generated by the ChipDNA circuit only when needed for encryption and is then instantly deleted. More important, the ChipDNA key never resides statically in registers or memory.
DS28E38 uses ChipDNA technology to cryptographically protect all data stored on the device. The device provides a set of cryptographic tools derived from integrated blocks, including an asymmetric hardware engine (ECC-P256), a random number generator compatible with FIPS/NIST (TRNG), 2kb of protected EEPROM, a counter and a unique 64-bit identification number (ROM ID).
Into Medicine
Health and wellness are one of the fastest growing applications for wearable IoT devices. Diabetes management is more efficient with wearable IoT devices, and soon many blood-related measurements will be possible through non-invasive means, using advanced detection applications.
Access to all of an individual’s personal health data is a major impetus to better health, but managing that access will be fundamental to personal privacy.
Security at both device and network level is essential for the operation of “objects”.
This does not require a revolutionary approach, but rather an evolution of measures that have shown success in computer networks adapted to the challenges of the embedded world.
Many integrated-processor providers – NXP, Maxim, Microchip, STMicroelectronics, Texas Instruments and others – have included dedicated encryption/decryption engines and random number generators on their ICs already, at the ready to protect the new generation of connected devices.









