Software-defined network architectures, driver assistance systems and digital twins are just a few example applications that need powerful hardware at the edge of the cloud to process data and task operations. The edge, in turn, demands much greater reliability, easy maintenance and extended components availability, but also a proper protection and securing of the data processed by its servers.
The cloud allows businesses to process even the largest data volumes with almost infinitely scaleable computing power. But for this to happen, the data must first be transferred to the cloud from the point of collection. The data then travels some way via the cloud, which is not suitable for applications such as autonomous vehicles, intelligent traffic systems and digital factories, as they require the lowest possible latencies – as near to real time as possible, to be able to take swift actions.
In addition, the data connection may potentially suffer unplanned or malicious disruptions and, of course, there’s the problem of limited bandwidth, which restricts data transport over existing network infrastructures. Hence, sending extremely large volumes of raw data to be processed in the cloud is not economically viable in many cases, and transmission costs and additional investments in infrastructure and connectivity are simply too high.
One solution is to use computing power with edge servers at the periphery of the cloud, to locally process the collected data. When increasingly-powerful server technology is moved to the edge, this also impacts the local infrastructure and network administration, since edge servers are also responsible for orchestrating the local networks. As a result, powerful systems for Network Function Virtualisation (NFV) and Software-Defined Networking – initially used mainly at the carrier or provider level – are now required in the industrial environment, too. These can be designed as standalone rugged appliances or consolidated directly in edge servers as virtualised systems.
Challenges at the edge
Edge server hardware, however, needs to meet significantly different requirements, such as environmental conditions – temperature, humidity, vibrations, etc. Systems like these are also expected to work non-stop, for extended periods of time, requiring long-term availability of their components.
Another important aspect in the network edge is data security; edge servers can be exposed to Internet attacks via WAN links.
Then, there’s the challenge of running different systems and applications, most likely from several customers or service providers, securely and separately on the same edge server and processor. This makes each of these virtual servers, right up to the hypervisor itself, a potential attack “surface” from where to infiltrate or manipulate other virtual machines, or to simply steal the data. In addition to the manufacturer-provided security APIs, all these challenges call for rugged and powerful embedded CPU platforms with effective hardware-enforced security features that protect against numerous attacks – including the notorious side-channel hacks. AMD has already integrated the necessary security features into the core architecture of its x86-based EPYC processor platforms and offers them in its AMD EPYC Embedded processors too, which are particularly well suited as server CPUs for harsh edge environments.
Hardware-enforced security
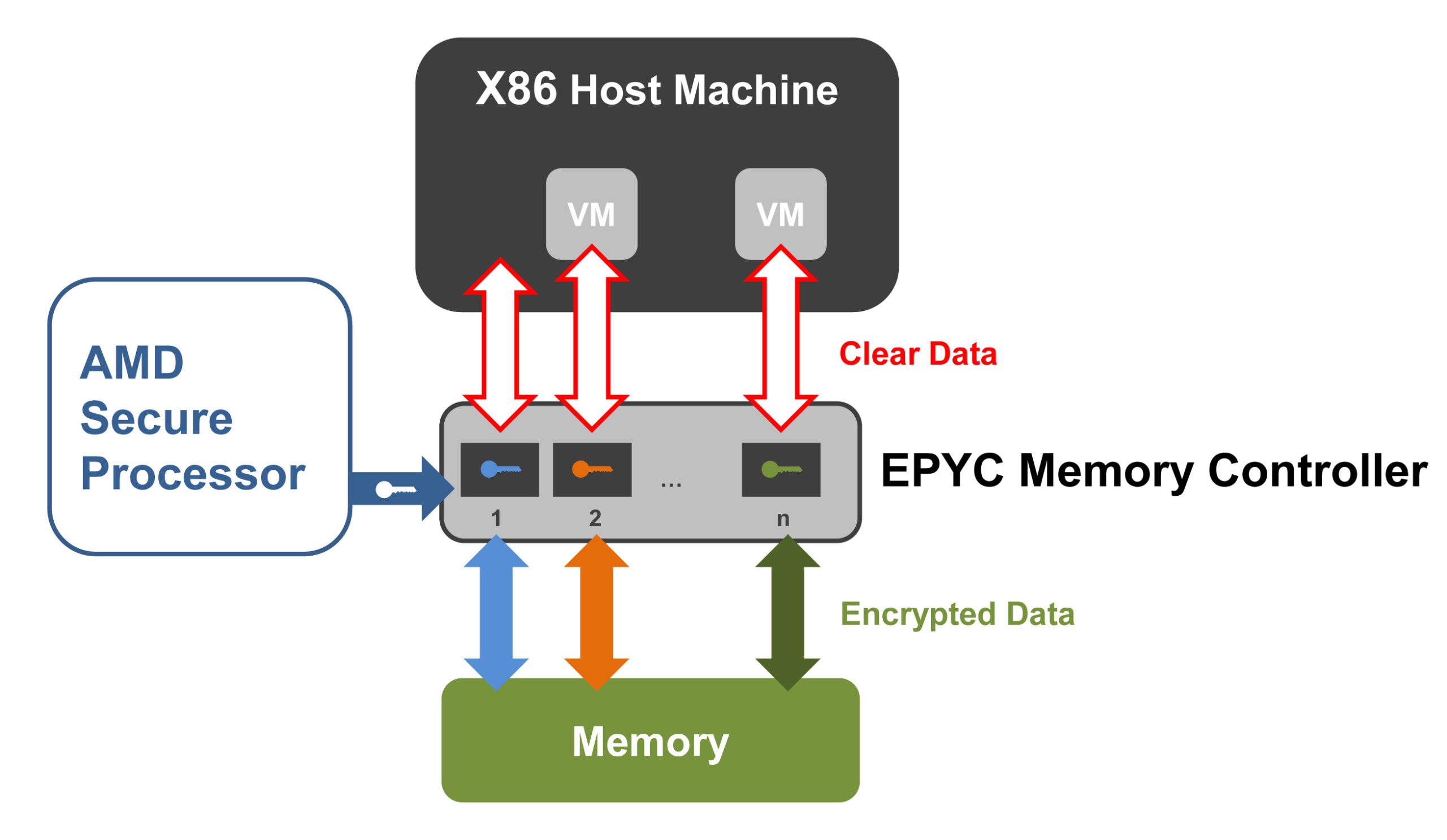
AMD has used its “Zen” microarchitecture to its server processor families EPYC Embedded 3000, 7001 and 7002, suitable for industrial edge servers, networks and storage devices. Now system developers can benefit from the same advantages that have made AMD EPYC processors so successful in data centres, with the additional benefits of extended availability and robustness. Particularly noteworthy are the integrated data-centre-grade security features that ensure the best possible protection of the processed data, even beyond confined data centre environments and difficult-to-monitor locations. The central element and root of trust is the dedicated AMD Secure Processor, which provides individual security features with AES‑128 keys that can’t be read by software, for example via a hypervisor, and are not even known to the CPU itself.
Secure Memory Encryption (SME), based on 128-bit AES keys that are activated via the BIOS settings; see Figure 1. If SME is enabled, the memory controller automatically encodes all contents stored in the memory via an AES-128 key assigned by the co-processor. This effectively protects the data in the working memory and cache from cold-start or platform-reset attacks – threats that occur at the edge.
The AMD Secure Processor also generates the AES keys for the Secure Encrypted Virtualisation (SEV), which allows each virtual machine (VM) running the EPYC CPUs be encrypted with its own unique key, known only to the processor the virtual machine is running on; see Figure 2. Even if a virtual machine has been compromised, the attacker can’t access the contents of the other VMs – and neither can the hardware-isolated key manager.
By activating an additional module, second-generation AMD EPYC processors from the 7002 Series can also encrypt the register that the hypervisor assigns to a VM. This feature, which AMD calls SEV Encrypted State (SEV-ES), uses a so-called Guest Hypervisor Communication Block (GHCB), which prevents CPU register data from being visible to other software components, including the hypervisor; see Figure 3. So, even if the hypervisor itself is compromised, it can’t access the memory contents of the VM because the GHCB only supplies encrypted contents in response to requests.
AMD SME is a default setting, but AMD SEV and SEV-ES require activation in the guest operating system and hypervisor; however, no change is necessary in the actual applications. So, if the hypervisor and OS support SEV, the customer application can take full advantage of these security features.
Choice of series
AMD provides a choice of three embedded EPYC series to design secure edge server applications, covering a gamut of performance requirements and applications. The latest family members – the EPYC Embedded 7002 Series – are available in nine different performance classes, and have availability of five years. They range from the octa-core 7262 device with a maximum clock speed of 3.4GHz and a thermal design power (TDP) of 155W, to the 7662 processor with 64 Zen 2 cores, 3.3GHz clock speed and TDP to 240W. All 7002 SoCs provide no fewer than 128 PCIe Gen-4 lanes and 32 SATA Gen-3 ports, in addition to 4x USB 3.1 Gen 1 and low-speed interfaces such as GPIO, I2C, LPC, SMBus, SPI and UART.
The EPYC Embedded 7001 Series processors also start from eight cores and go to 32 cores in the 7601 device. They, too, offer similar features, with their TDP ranging from 120W to 180W; their cooling demands are, however, much lower compared to those of the 7002 Series.
When it comes to extremely harsh environments or temperatures ranges anywhere from -40°C to 85°C, the EPYC Embedded 3000 processors meet these demands: With up to 16 Zen cores and flexible I/Os, they offer an ideal combination of performance and resilience for embedded designs.
By Electronics World editors