By Scott Jones, Managing Director, Embedded Security, Maxim Integrated
From toys to refrigerators to cars, the connected devices in our lives are increasing in volume, and medical devices are no exception. While intelligence and connectivity bring great convenience in monitoring patients’ wellbeing, they can also bring malicious attacks.
Many pundits have already raised the red flag on medical devices as the next potential security concern. A hacked security camera or even a toy can expose users to privacy breaches, and this is very worrisome. Imagine the ramifications if a cybercriminal gained control of something like a pacemaker or an insulin pump! Such incidents have already come to light:
- In 2007, the cardiologist of former US Vice President Dick Cheney requested the manufacturer of Cheney’s implanted heart defibrillator to disable the wireless feature to prevent hacking.
- In September 2017, the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), which is part of the US Department of Homeland Security, reported a security flaw in syringe infusion pumps discovered by an independent security researcher, where a hacker could potentially change the quantities of medication administered to a patient.
- Another device manufacturer is dealing with lawsuits related to vulnerabilities in its implantable cardiac defibrillators and pacemakers, some of which have been recalled.
- There are reports that British and Belgian researchers have uncovered security flaws in the proprietary communication protocols of ten implantable cardiac defibrillators on the market.

Taking Steps
These are just a few examples highlighting the risks for the industry. A Ponemon Institute study released in May 2017, called “Medical Device Security: An Industry Under Attack and Unprepared to Defend”, reported that while 67% of medical device makers anticipate an attack on their devices over the next year, only 17% of them were taking significant steps to prevent such an incident.
Another alarming finding of the study is that only one-third of device makers surveyed reported that their organisations encrypt traffic among Internet of Things (IoT) devices and only 29% of healthcare delivery organisations use encryption to protect data transmitted from medical devices. In fact, only about one third of those surveyed were even aware of potential adverse effects on patients stemming from insecure medical devices.
When it comes to implementing security, there are persistent myths that may be preventing developers from proactively protecting their devices. Many believe that implementing security is expensive, time-consuming and difficult. These beliefs prevent device developers from acting in the first place. When you take a closer look at the techniques and technologies available now, however, it’s quite clear how easy it can be to strongly protect medical devices from cybercriminals.
With features such as wireless connectivity, health-monitoring sensors and near-field communication (NFC) integrated into medical devices, healthcare professionals can easily keep tabs on their patients, wherever they are. Patients can also conveniently track their own wellbeing.
There are implantable medical devices that monitor health parameters and deliver medication; connected devices that track adherence to prescribed treatments; ingestible sensors that also monitor adherence; and many more. These smart, connected devices are continually collecting and sending data wirelessly to medical professionals, enabling a more proactive, coordinated approach to care and streamlining medical costs. And with the connected technology, medical care is expanding to people with impaired mobility.
Risk Scenarios for Medical Endpoints
In its report “Internet of Medical Things, Forecast to 2021”, Frost & Sullivan projects that the number of IoMT devices could grow to 30 billion by 2020, from 4.5 billion in 2015.
If not secure, any of these devices could be a target for a hacker, and what if a cybercriminal uses the hacked device to gain entry into, say, a hospital’s network, stealing sensitive data to file false medical insurance claims or purchase pharmaceuticals?
For the device manufacturer, a breach could open the door to theft of intellectual property (IP) and lost revenue if, say, the attacker creates counterfeit versions of devices. Medical endpoints, including tools, sensors and consumables, face these potential risk scenarios:
- Introduction of a virus or harmful configuration data;
- Re-use of limited-life endpoint peripherals beyond their targeted lifecycle, creating unsafe situations;
- Counterfeiting, where fake devices and sensor endpoints have falsified or altered the data produced by a real one.
Regulatory agencies worldwide are sounding an alarm to device developers. The US Food and Drug Administration (FDA), for example, encourages what it calls a “total product lifecycle approach” when it comes to securing medical devices. Security should be built in as soon as the product design phase begins; there should be a plan to manage any risks that might emerge, as well as one that outlines ways to reduce the likelihood of future risks, according to the FDA.
The European Union Agency for Network and Information Security (ENISA) cites these FDA medical device cybersecurity measures for guidance. In Asia, the China Food and Drug Administration (CFDA) has called on medical device developers to assess security of each device in question in the context in which it will be used, and take appropriate risk-control measures.
I Am The Cavalry, a grassroots organisation formed in 2013 to focus on issues where computer security intersects public safety and human life, has issued a Hippocratic Oath for Connected Medical Devices. This oath urges stakeholders to support a set of principles:
- Cyber safety by design;
- Disclosure of potential safety or security issues to third parties;
- Evidence capture, preservation and analysis to learn from safety investigations;
- Safeguarding critical elements of care delivery in adverse conditions;
- Prompt, agile and secure updates.
The oath was developed collaboratively with cybersecurity researchers and those working within the healthcare ecosystem. Its aim is to preserve patient safety and trust in the process of care delivery.
Techniques for Safeguarding Medical Devices
So what kind of risk-control measures are suitable for medical devices? Software-based security is considered cost-effective and relatively easy to use; however, it is also easy to modify and readily susceptible to malware.
Hardware-based security has proven itself far stronger, as it’s difficult to alter the physical layer. Secure ICs with a root of trust are particularly robust. For example, with a microcontroller, the root of trust could be startup code stored in internal immutable ROM, used to verify and authenticate an application’s software signature when the microcontroller is powered on; the root of trust cannot be modified. By implementing hardware-based root of trust from the bottom up, developers can close off more potential entry points into their design. In fact, it really is the only solution that guards against attacks that attempt to breach the casing of an electronic device.
Next-generation hardware security based on physically unclonable function (PUF) technology provides an even stronger level of protection. PUF circuitry uses the random electrical properties of IC devices, producing a unique and repeatable root cryptographic key for each IC. Even though different ICs may share the same mask and manufacturing process, each IC is slightly different based on normal manufacturing variability. By tapping into this variability, PUF circuits can extract secret information that is unique to each chip.
Gate delay, the power-on state of SRAM and random mismatch of analogue circuits are among the many physical characteristics that can be used to derive the secret code. The key is generated only when needed through analysis of a variety of PUF elements, and it is never stored anywhere on the chip. As such, a device featuring this technology cannot succumb to an invasive attack. Even when attacked via techniques like de-processing or micro-probing, this will change the circuit’s electrical characteristics to a point that further attack is prevented.
Sub-$1 secure authenticators with PUF technology are now available. With fixed-function operation and no device-level programming, these authenticators can easily be integrated into an embedded design.
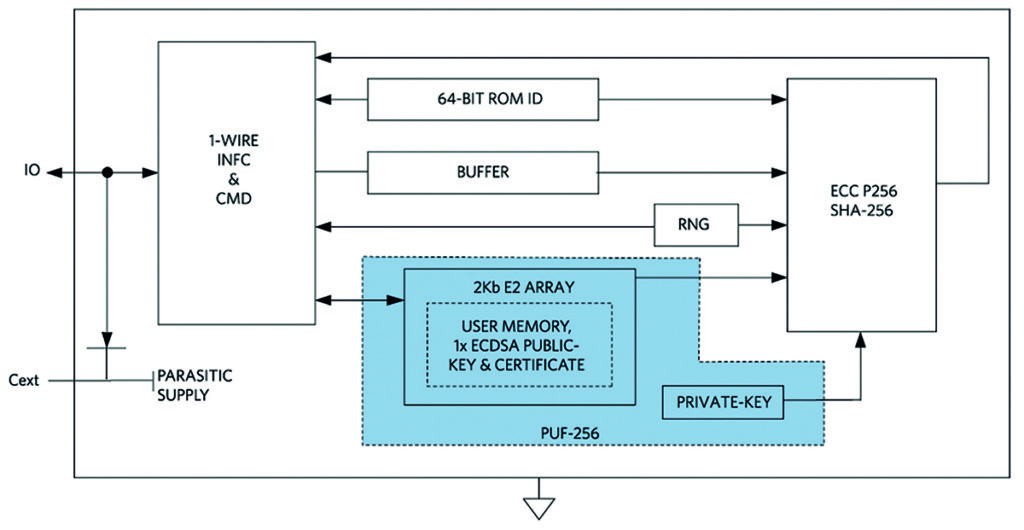
Secure Authentication Prevents Counterfeiting
Secure authentication technology provides many benefits, including traceability, usage and secure monitoring, and safeguards against counterfeiting. For example, consider a connected blood glucose meter, from which data is transferred to a smartphone and then to a patient’s record at a medical facility. Authentication provides traceability by verifying that the data came from a specific device.
As an example of secure monitoring, consider a medical consumable. Secure authentication can verify the consumable and provide authenticated usage information back to a central processing site for transfer to a patient’s record. Many medical devices are designed for single use only. Challenge-and-response authentication can be implemented to ensure that the tool, like a surgical instrument, is both authentic and hasn’t been used before.
Challenge-and-response authentication is considered a robust methodology for our digital world, much more secure than password-based authentication, as passwords can easily be intercepted. Challenge-response authentication can be due to symmetric or asymmetric cryptography. In symmetric cryptography-based authentication, the host and the device to be authenticated have a shared secret key.
The host sends a challenge in the form of a random number to the device. The device then computes a digital signature as a function of the secret and the challenge, sending it back to the host, which runs the same computation, comparing the results. If there’s a match, the device is authenticated.
Secure hash functions, such as SHA-256, provide the mathematics to ensure a device will be able to prove its secret without disclosing it; see Table 1 for an overview of some popular cryptographic algorithms supported by secure authenticators.
| Algorithm | NIST Standard |
| SHA-256 MAC | FIPS 180 |
| SHA-256 HMAC | FIPS 198 |
| ECDSA-P256 | FIPS 186 |
| ECDH-P256 | SP 800-56A |
In asymmetric cryptography, there’s a private key and a public key. Only the device to be authenticated knows the private key. The public key can be shared with any entity that seeks to authenticate the device. Here, the host sends a challenge to the device, which computes a signature based on this challenge and its private key, and sends the result back to the host. The host then uses the public key to verify the signature.
The function used here to compute the signature must have certain mathematical properties, which are commonly used functions for asymmetric cryptography are RSA and ECDSA. Embedded security ICs that support SHA-256 and ECDSA can be integrated into a medical device design, for protection from the ground up.
Added Security
While secure microcontrollers and authenticators and other embedded security ICs can protect the medical device designs themselves, other measures can further safeguard the IoMT from malicious attacks. Separating the medical network of devices from the network for PCs, laptops and databases can hamper attempts to break into a compromised device. This way, if a connected medical device gets hacked, the attack won’t fully unfold.
It’s also important to protect the software applications that run on connected medical devices, preventing copying, tampering or the insertion of malicious code.
Strong authorisation protocols are another essential tactic to minimise the chances of a device getting hacked.
By designing embedded security ICs into medical devices from the very beginning, developers can prevent costly problems later on.










